Publications
My Google Scholar profile link
R. Yasaei, Sina Faezi, M. Al Faruque, “Golden Reference-Free Hardware Trojan Localization using Graph Convolutional Network”, IEEE Transactions on Very Large Scale Integration Systems (TVLSI’22), 2022.
R. Yasaei, Luke Chen, Shih-Yuan Yu, M. Al Faruque, “Hardware Trojan Detection using Graph Neural
Networks”, IEEE Transactions on Computer-Aided Design of Integrated Circuits and Systems (TCAD’22), 2022. download pdf
R. Yasaei, S. Yu, E. Kasaeyan Naeini, M. Al Faruque “GNN4IP: Graph Neural Network for Hardware Intellectual Property Piracy Detection”, Design Automation Conference (DAC’21), 2021. download pdf

R. Yasaei, S. Yu, M. Al Faruque, “GNN4TJ: Graph Neural Networks for Hardware Trojan Detection at Register Transfer Level”, IEEE/ACM Design Automation and Test in Europe Conference (DATE’21), 2021. download pdf

S. Faezi, R. Yasaei, M. Al Faruque, ” HTnet: Transfer Learning for Golden Chip-Free Hardware Trojan Detection”, IEEE/ACM Design Automation and Test in Europe Conference (DATE’21), 2021. download pdf
S. Yu, R. Yasaei, Q. Zhou, T. Nguyen, M. Al Faruque, “HW2VEC: A Graph Learning Tool for Automating Hardware Security”, IEEE International Symposium on Hardware Oriented Security and Trust (HOST 2021). download pdf
Y. Zhang, R. Yasaei, H. Chen, Z. Li, M. Al Faruque, “Stealing Neural Network Structure through Remote FPGA Side-channel Analysis”, IEEE Transactions on Information Forensics and Security (IEEE TIFS’21), 2021.
S. Faezi, R. Yasaei, A. Barua, M. Al Faruque, “Brain-Inspired Golden Chip Free Hardware Trojan Detection”, IEEE Transactions on Information Forensics and Security (TIFS’21), 2021. download pdf

R. Yasaei, F. Hernandez, M. Al Faruque, “CAD-IoT: Context-Aware Adaptive Anomaly Detection in IoT through Sensor Association”, accepted in IEEE/ACM International Conference On Computer-Aided Design (ICCAD’20), 2020. download pdf
Y. Zhang, R. Yasaei, H. Chen, Z. Li, M. Al Faruque, “Poster: Stealing Neural Network Structure through Remote FPGA Side-channel Analysis”, ACM/SIGDA International Symposium on Field-Programmable Gate Arrays (FPGA’21), 2021.

R. Yasaei, S. Faezi, M. Al Faruque, “Poster: Golden chip-Free Hardware Trojan Detection in Run-time using Transfer Learning”, presented in Design Automation Conference (DAC’20), 2020.
R. Yasaei, S. Yu, M. Al Faruque, “Poster: Graph Learning for Hardware Trojan Detection”, Women in Hardware and Systems Security Workshop (WISE’20), 2020.

R. Yasaei, S. Faezi, M. Al Faruque, “Poster: Golden-chip Free Approach for Hardware Trojan Detection in Run-time”, presented in Design Automation Conference (DAC’19), 2019.
Tools and Datasets
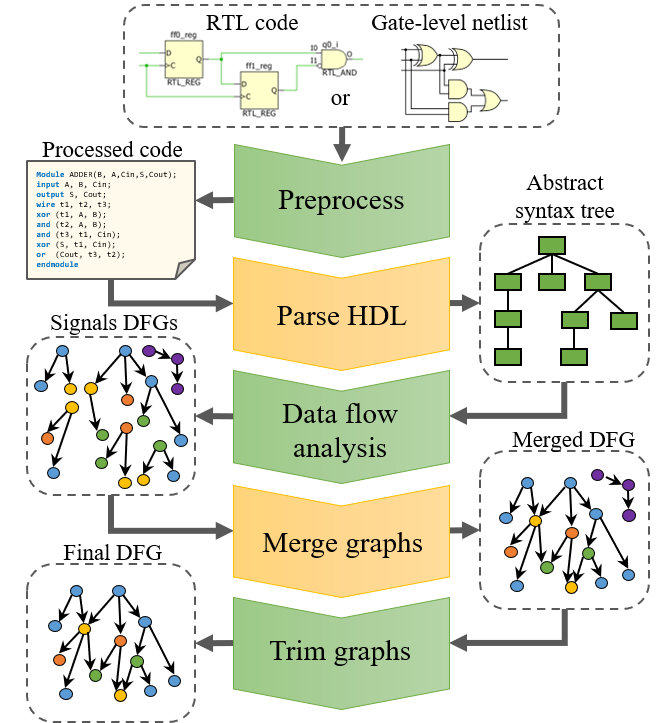
Hardware Design Dataset for Circuit Graph Learning
Citation Authors: Rozhin Yasaei, Shih-Yuan Yu, Mohammad Abdullah Al Faruque
Access Link: IEEE-Data port
License: Creative Commons Attribution
Keywords: Hardware Security, Representation Learning, Graph Embedding
User Documents: supporting documents
Paper Citation and Link: Yu, Shih-Yuan, et al. “HW2VEC: A Graph Learning Tool for Automating Hardware Security.” arXiv preprint arXiv:2107.12328 (2021). Link
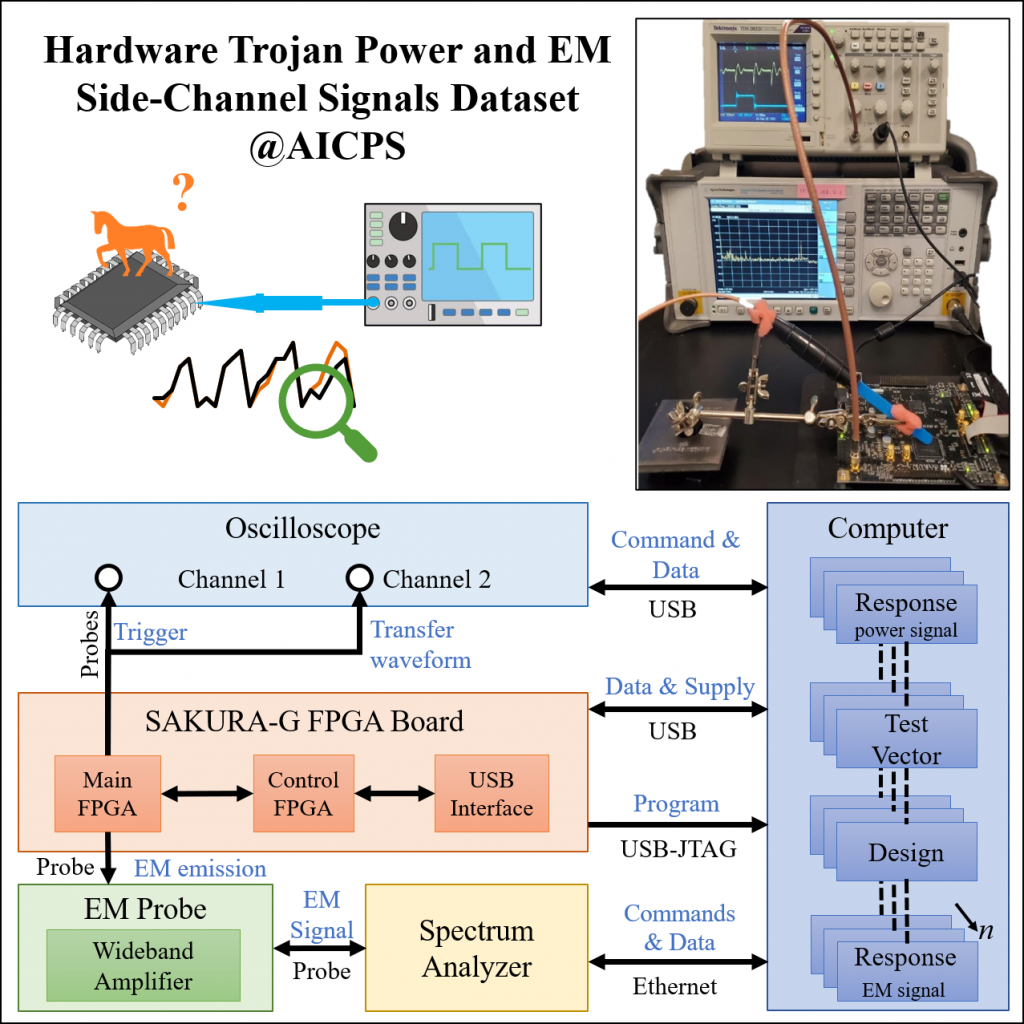
Power and EM Side-Channel for Hardware Trojan Dataset
Citation Authors: Rozhin Yasaei, Sina Faezi, Mohammad Abdullah Al Faruque
Access Link: IEEE-Dataport
DOI: 10.21227/9fwb-8978
Data Format: *.csv
License: Creative Commons Attribution
Keywords: Side-Channel Signal, Power Consumption, Electromagnetics, Hardware Trojan, Hardware Security.
Abstract:
Design and fabrication outsourcing has made integrated circuits vulnerable to malicious modifications by third parties known as hardware Trojan (HT). Over the last decade, the use of side-channel measurements for detecting the malicious manipulation of the chip has been extensively studied. However, the suggested approaches mostly suffer from two major limitations: reliance on trusted identical chip (e.i. golden chip); untraceable footprints of subtle hardware Trojans which remain inactive during the testing phase. To overcome these shortcomings, we propose a novel idea of maintaining a dynamic model of the integrated circuit throughout its life cycle for the purpose of detecting HT that might have been injected anywhere in the supply chain. In this paper, we gather a comprehensive dataset of power and Electromagnetic (EM) side-channel signals for hardware Trojan benchmarks from Trust Hub benchmarks to develop a statistical model of the chip for HT detection. To be used in a golden chip-free Trojan detection approach, the side-channel data is collected in the presence of HT under two scenarios: when the HT is inactive and when it is activated. Consequently, all the measured power data include the static power of HT in addition to base circuit power consumption, which makes the detection more challenging. The only difference between the two data collection scenarios is the dynamic power consumption of HT.
– For further information, see the supporting documents.
– Please cite the following papers when using any data from this dataset:
Faezi, Rozhin Yasaei, Anomadarshi Barua, Mohammad Abdullah Al Faruque, “Brain-Inspired Golden Chip Free Hardware Trojan Detection”, IEEE Transaction on Information Forensics and Security (IEEE TIFS’21), 2021.
– This research was supported by the Office of Naval Research (ONR) award N00014-17-1-2499.